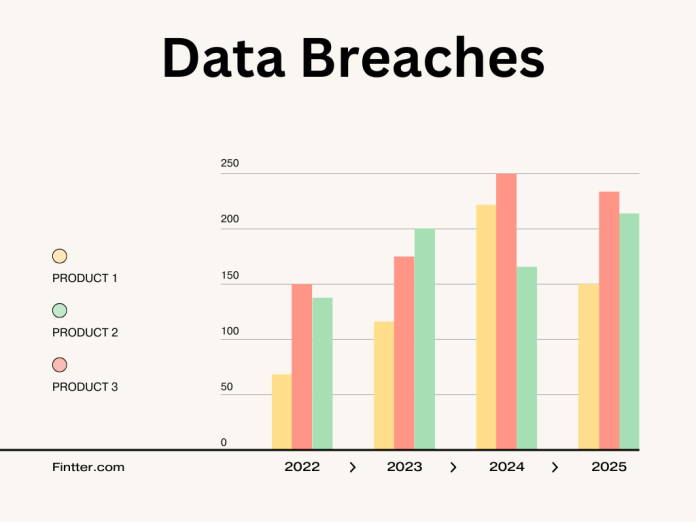
In today’s digital world, data breaches are becoming more common and more costly. From high-profile incidents involving major corporations to smaller, unnoticed attacks, cybercriminals are increasingly targeting sensitive information. The financial, legal, and reputational impacts of these breaches are devastating, making robust cybersecurity practices a necessity for every organization and individual.
In this blog tutorial, we’ll take a closer look at the factors contributing to the rise of data breaches, the consequences of these attacks, and how cybersecurity measures can help protect against them. Let’s dive in!
1. The Growing Problem of Data Breaches
A data breach occurs when unauthorized individuals access sensitive information, such as personal data, financial details, login credentials, or proprietary company data. These breaches can happen for a variety of reasons, including system vulnerabilities, weak passwords, insider threats, and sophisticated hacking attempts.
Over the past few years, the number of data breaches has skyrocketed, largely due to:
- Increased Cybercrime: Cybercriminals are becoming more organized, and their attacks more sophisticated, using techniques like ransomware, social engineering, and phishing to exploit vulnerabilities.
- More Valuable Data: With the rise of big data, AI, and IoT, the value of personal and organizational data has increased. This makes it an attractive target for cybercriminals who are looking to steal data for profit.
- Remote Work and Cloud Usage: As organizations shift to cloud-based platforms and remote work becomes the norm, cybersecurity gaps and misconfigurations have become common entry points for hackers.
- IoT and Connected Devices: The growing number of connected devices, from home appliances to wearable tech, creates more entry points for hackers to exploit.
2. The Consequences of Data Breaches
The fallout from a data breach can be severe, and the effects can be long-lasting. Here are some of the primary consequences that businesses and individuals face:
a. Financial Loss
One of the most immediate consequences of a data breach is the financial cost. Businesses may face regulatory fines, lawsuit settlements, and remediation costs, which can add up to millions of dollars. Additionally, the loss of intellectual property or trade secrets can lead to competitive disadvantages.
For individuals, financial loss can come in the form of identity theft, unauthorized transactions, and the need for costly credit monitoring or identity theft protection services.
b. Reputational Damage
Data breaches can cause significant damage to a company’s reputation. Consumers are more likely to trust brands that protect their data, and a breach can erode that trust. Even with an effective response, the damage to a company’s reputation can linger long after the breach is contained, resulting in loss of customers and revenue.
c. Legal and Regulatory Ramifications
In many regions, laws such as the General Data Protection Regulation (GDPR) in the EU and the California Consumer Privacy Act (CCPA) in the US hold businesses accountable for protecting customer data. A data breach can lead to legal action from affected individuals or regulatory fines if companies fail to comply with these privacy regulations.
d. Loss of Competitive Advantage
For businesses, a data breach can result in the theft of intellectual property, trade secrets, or customer data, all of which may provide a competitive edge. When these assets fall into the wrong hands, companies can lose their market position.
3. How Cybersecurity Can Keep You Safe
The rise of data breaches has highlighted the need for comprehensive cybersecurity measures. While no system can be completely impervious to attack, robust security practices can significantly reduce the risk of a breach and mitigate its impact if one occurs. Here are the key strategies businesses and individuals should adopt to protect against data breaches:
a. Strong Password Management and Multi-Factor Authentication (MFA)
Passwords remain one of the most common weak points in cybersecurity. To reduce the risk of unauthorized access, users should implement strong password policies. This includes using long, complex passwords, changing passwords regularly, and avoiding password reuse.
Multi-factor authentication (MFA) is a must. By requiring users to provide two or more verification factors (something you know, something you have, or something you are), MFA significantly reduces the chances of unauthorized access to sensitive data.
b. Encryption
Data encryption is one of the most effective ways to protect sensitive information. Encrypting data makes it unreadable to anyone who does not have the decryption key, even if they manage to steal the data. This should be implemented both for data in transit (as it moves across networks) and data at rest (when it is stored on servers or devices).
c. Regular Software Updates and Patch Management
Outdated software and unpatched vulnerabilities are a common entry point for cybercriminals. Ensuring that your operating systems, applications, and devices are up-to-date with the latest security patches is essential for defending against known exploits. Set up automatic updates whenever possible to keep systems secure.
d. Employee Education and Awareness
Human error is one of the leading causes of data breaches. Employees may unknowingly fall victim to phishing emails or other social engineering tactics that expose sensitive information. Regular training and awareness programs are critical in teaching employees how to recognize phishing attempts, avoid suspicious links, and follow proper security procedures.
e. Data Backup and Disaster Recovery Planning
In the event of a data breach, having a comprehensive disaster recovery plan (DRP) in place is essential. Businesses should regularly back up critical data and store it securely, separate from the primary system, and ensure that they can quickly restore lost or compromised data.
Additionally, organizations should have a breach response plan in place, including communication strategies for informing customers, regulators, and other stakeholders. Being prepared can minimize downtime and reduce the impact of a breach.
f. Network Security and Firewalls
A strong network security posture is essential for preventing unauthorized access to company systems. Firewalls and intrusion detection systems (IDS) are the first line of defense against cyberattacks. These tools monitor network traffic for suspicious activity and can automatically block or alert administrators to potential threats.
Furthermore, businesses should implement segmentation within their networks to limit the movement of attackers. By isolating critical systems and data, organizations can reduce the potential damage caused by a breach.
g. Cloud Security and Misconfiguration Management
With the growing adoption of cloud services, many businesses are storing sensitive data off-site. Cloud providers offer robust security measures, but businesses must also ensure that their own cloud security settings are configured correctly. Misconfigurations, such as exposed cloud storage, are a common cause of data breaches.
Organizations should conduct regular audits of their cloud environments and use encryption to protect cloud data. Additionally, it’s crucial to implement strong access control policies and ensure that only authorized personnel can access sensitive information.
4. Responding to a Data Breach: A Quick Guide
Despite all preventive measures, no system is completely secure. If a data breach occurs, responding quickly and effectively is critical to minimize damage. Here’s a brief guide on how to respond to a data breach:
- Contain the Breach: Identify the source and stop the breach as quickly as possible. This may involve disconnecting affected systems from the network.
- Assess the Impact: Determine what data was compromised and who was affected. This will help guide your response and notification process.
- Notify Stakeholders: Inform affected customers, regulators, and other stakeholders about the breach. Transparency is key to maintaining trust.
- Mitigate Damage: Offer support, such as free credit monitoring for affected individuals, and take steps to prevent similar breaches in the future.
- Conduct a Post-Incident Analysis: After the breach has been contained, perform a thorough investigation to identify weaknesses and improve your cybersecurity measures.
5. Conclusion
Data breaches are an ever-present threat to businesses and individuals alike. As cybercriminals become more sophisticated, the consequences of these breaches are growing more severe. However, by implementing robust cybersecurity practices, such as strong password management, encryption, employee training, and regular software updates, we can significantly reduce the risk of a breach.
Moreover, having an incident response plan in place and being prepared to act quickly can help minimize the impact of a data breach. The key to protecting yourself and your organization from the rising tide of cyberattacks is staying vigilant, proactive, and always ready to adapt to new threats.